RADIUS With Windows Server 2012R2
- 22 July 2016
- #security
- #ed-itsolutions
RADIUS is a form of network security that can link into your Windows Domain. The most common use (at least in my experience) is to secure Wireless Networks. Using RADIUS has the advantage of no shared key that has to be entered on each device, you can allow all domain computers to connect with their computer account and limit users to some trusted staff who only need their domain account to connect.
Before I started I had a fully functioning Windows Domain Controller with AD setup for normal use.
ADCS
Active Directory Certificate Services is used to generate the certificate that your RADIUS server will use to identify itself.
Open the Add Roles and Features wizard from server manager, select your DC and tick Active Directory Certificate Services.
Agree to the required features and click next. Click next again on the features screen and again on the AD CS screen.
On the Role Services screen you only need Certification Authority ticked.
Click Next and then confirm the install.
Once the install finishes click Configure Active Directory Certificate Services on the destination server.
In the wizard that pops up select the user you want to install the service as (in my case it was the same as my logged in user) and hit next.
When asked to Select Role Services to configure tick Certification Authority.
Select Enterprise CA and hit next, then select Root CA and hit next.
Select Create a new private key and hit next. On the Cryptographic screen change the hash algorithm from the insecure sha1 to sha256 and click next.
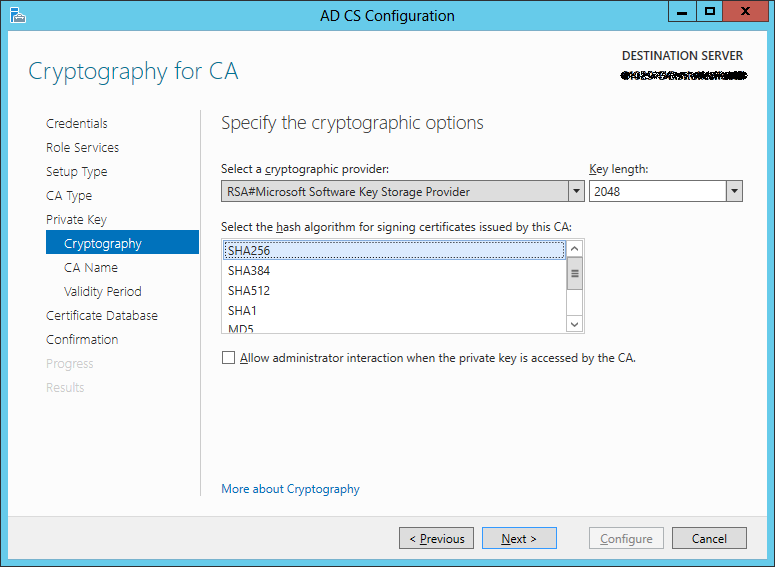
Leave the CA Name at the default and hit next, do the same with the validity period and database location.
On the Confirmation screen make sure that everything is as it should be and then hit Configure.
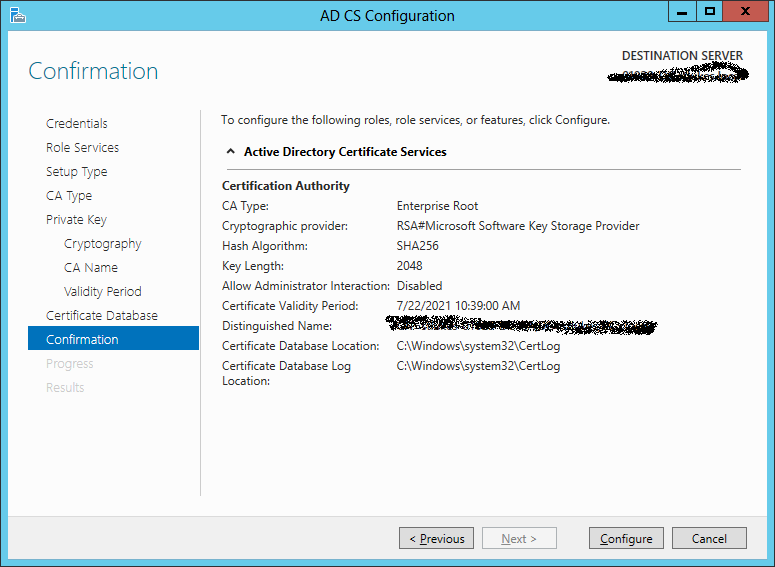
After configuration completes hit close.
NPAS
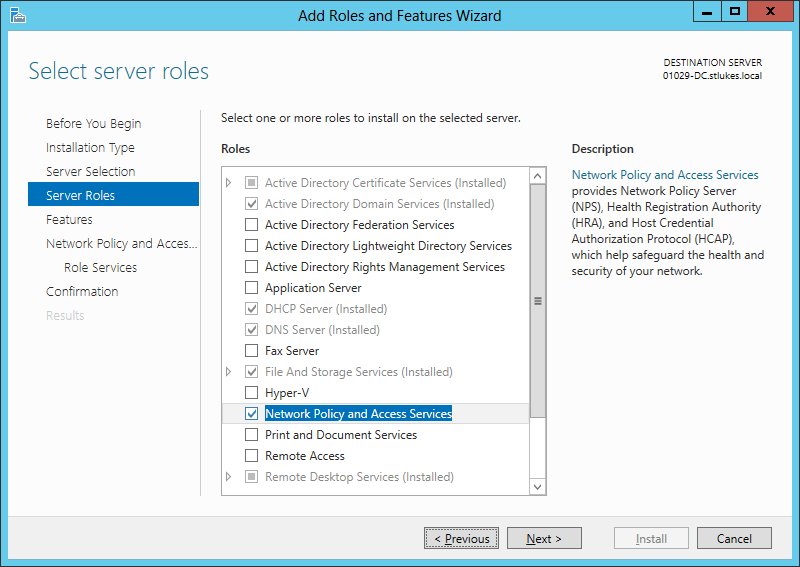
RADIUS is part of the Network Policy and Access Services role in Server 2008+ and is installed like the ADSC role.
Go to the Select Server Roles screen and tick Network Policy and Access Services, agree to the required features and hit next.
Hit next on the Features screen and again on the NPAS introduction.
On the Role Services screen you only need Network Policy Server selected.
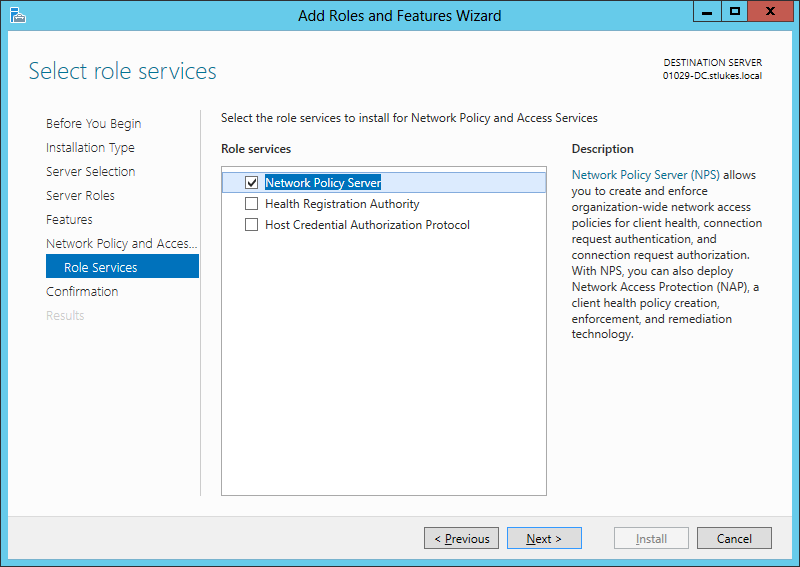
On the Confirmation screen hit Install.
After the install finishes you can hit Close.
Open Network Policy Server from the start menu and before you configure your RADIUS network right click Templates Management -> Shared Secrets and select New.
Give your Key a name and either type in or generate a secret.
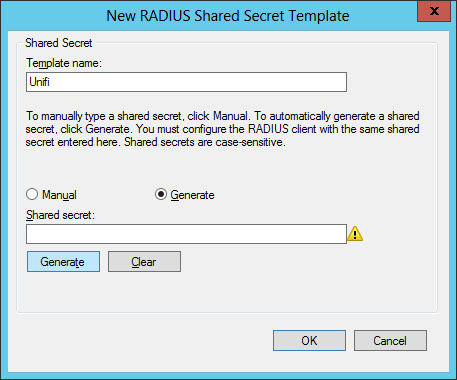
At this point I normally go into my Wireless system and create the new RADIUS network whilst I have my generated key in the clipboard.
With that template created head back to the main NPS screen and select RADIUS server for 802.1X Wireless or Wired Connections and click Configure 802.1X under it.
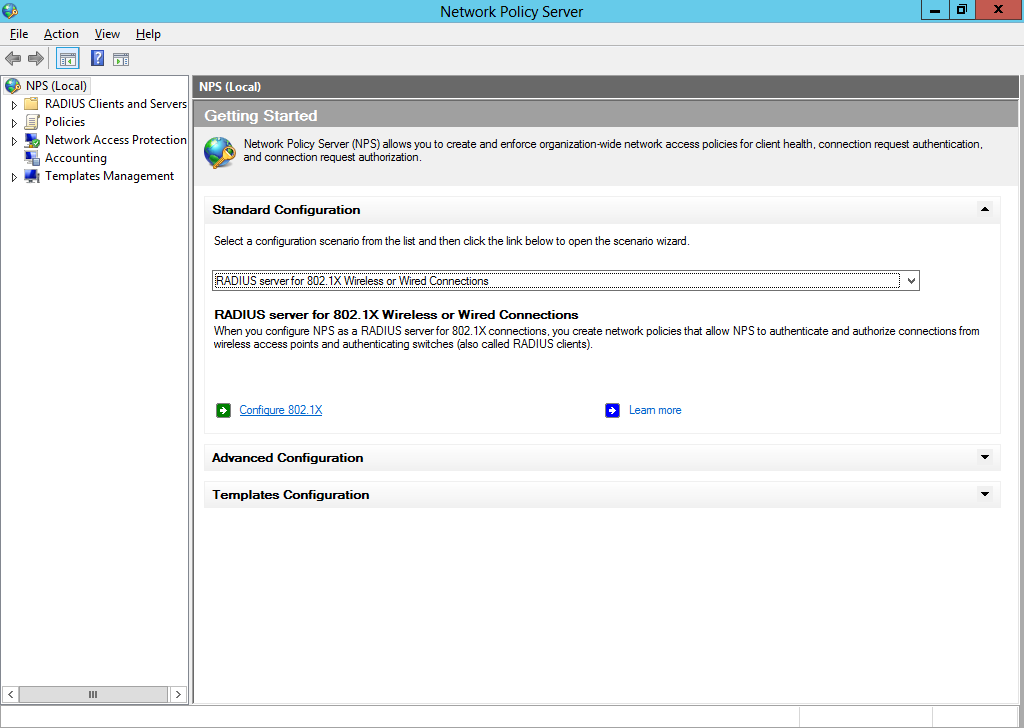
Select Secure Wireless Connections and click next (you can change the name if you want to).
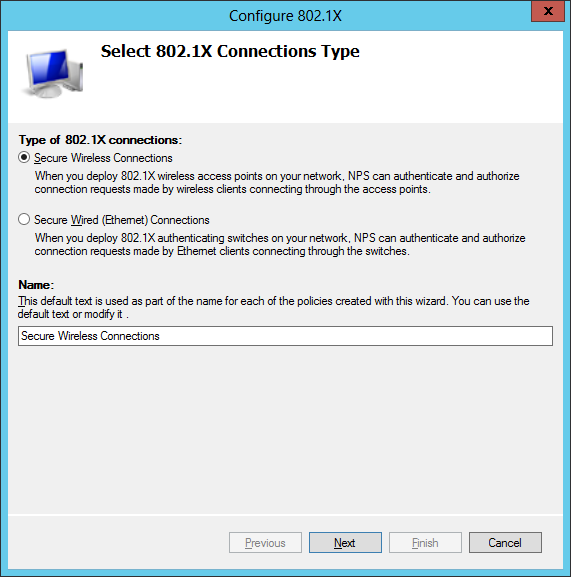
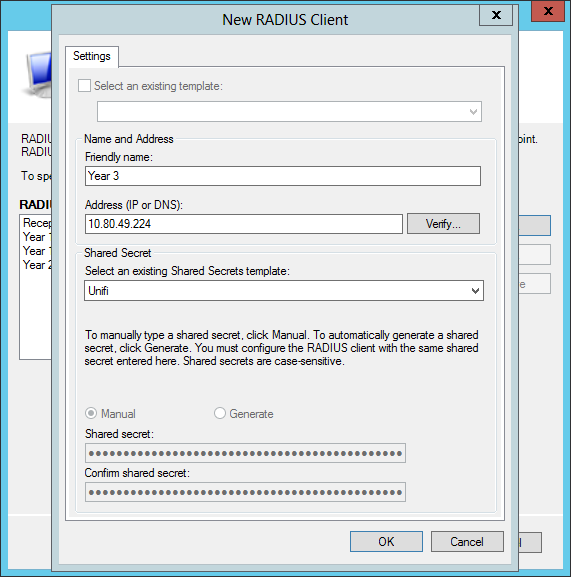
You need to add each access point to the list which can be pretty tedious.
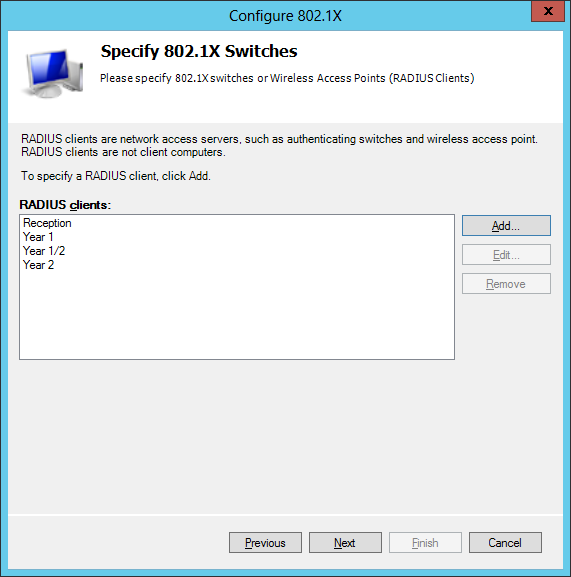
When adding an AP select the shared secret template we made earlier. Once you have added all your access points hit next.
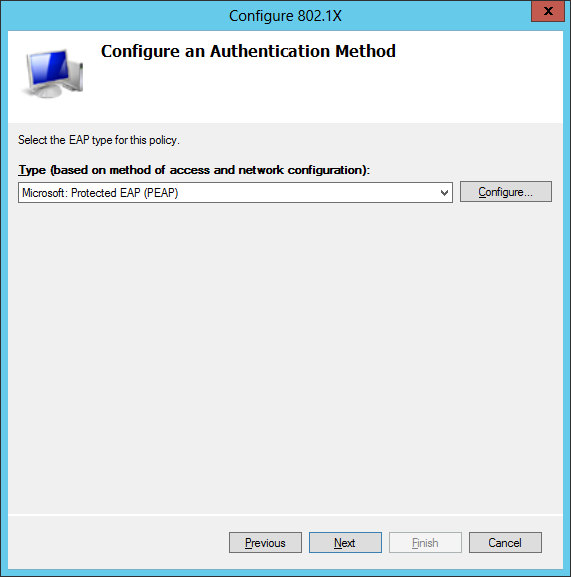
On the Configure an Authentication Method screen select Microsoft: Protected EAP (PEAP) and click Configure.
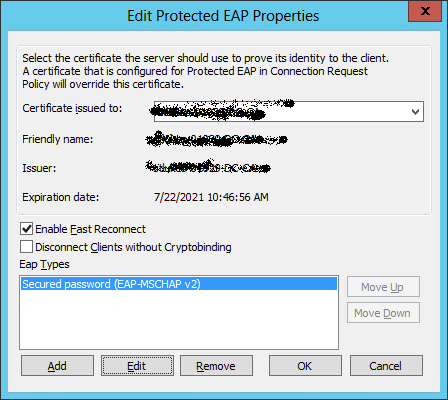
Change to the certificate for your DC, dc.domain.local NOT domain-dc-ca.
On the Specify User Groups screen add your Domain Users and Domain Computers groups and click next.
Click next on the Configure Traffic Controls screen.
On the last screen confirm all the details and then hit finish.
Done
You now have a RADIUS a network! Domain joined computers can now connect with seemingly no password as their computer account allows them to authenticate. None domain devices can authenticate with any user account.
